Vehicle Cyber Security (UK) with expert Ken Munro
In response to the growing concern over vehicle theft, we recently hosted a webinar featuring Ken Munro an expert in vehicle cyber security. The focus of the session was to break down recent trends, identify vulnerable vehicle models, and discuss new security measures. Below are the key take-aways on how customers can protect their vehicles from evolving threats.
The size of the problem
In the last few years there has been a significant increase in car theft. So much so that it has become a frequent topic of interest in the media. Below are examples of recent headlines including “Most Stolen cars of 2023 Revealed”, where the Ford Fiesta was noted to be the most stolen vehicle in the UK.
The key consideration for us, as insurers, is not the total number of cars stolen but trends such as theft frequency. This refers to the proportion of a specific make and model that are stolen within a given time frame, relative to the total number of those vehicles registered in the UK.
Theft frequency trends for all cars registered in the UK over recent years reveals a significant drop in 2020 due to COVID-19. However, since then, there have been noticeable increases, with projections indicating a potential 42% rise by 2024 compared to pre-pandemic levels.
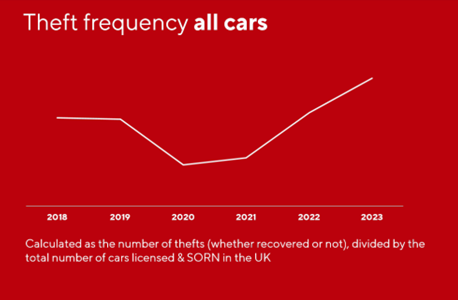
Analysis reveals an increase in theft frequencies. Manufacturers like Jaguar Land Rover and Nexus are addressing these concerns.
Legislative efforts are underway to ban electronic devices used for car thefts. Electric vehicles (EVs), notably Tesla and Polestar models, generally show lower theft frequencies due to advanced theft protections like PIN to drive and sentry mode, making them less appealing to thieves in certain areas.
We sought advice from a seasoned expert
To help tackle these risks and understand its complexity, we have sought the advice from a seasoned expert, Ken Munro. Ken is an ethical hacker working at Pen Test Partners, he, and his team search for vulnerabilities in organisation’s systems before cybercriminals do. They're hired by organisations to test their security, showing them how they could be breached, and allowing fixes to be put in place. They focus on various technologies like connected home devices, and vehicles to improve digital safety.
Technological advancements in vehicles
The industry has seen some exciting advancements, such as the Internet Of Things (IoT), electrification, Artificial Intelligence (AI), human-machine interfaces, vehicle connectivity, and even autonomous vehicles, however, these come with their own challenges, specifically cyber-attacks. As tech evolves, consumers seek advanced features like navigation and real-time tracking, yet integrating such connectivity, raises security and privacy concerns. Concerning incidents like the ‘Jeep hack’ by Miller & Valasek and the ‘Moss transponder hack’ in Volkswagen (VW) vehicles highlighted critical flaws which resulted in widespread motor recalls. Emerging threats like the "roll jam" attack highlights that securing vehicle systems still face ongoing challenges.
Ken shared that the theft of a friend’s Rav Four, caught on CCTV, revealed a huge vulnerability developed by injecting products into vehicle systems through a cars headlight, enabled by widely accessible hacking tools in the form of smart speakers.
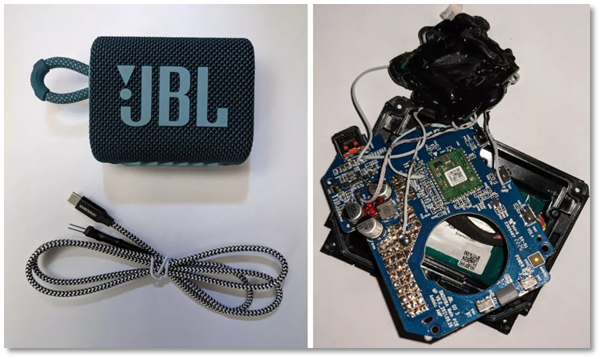
Ken's investigation into connected vehicles, started with BMW's i3 and i7 where he uncovered concerns in early electric cars' mobile apps, which were allowing unauthorised access and the capability to manipulate of vehicle systems.

The issue with the mobile apps was the ability to bypass logins and gain access to people's accounts by initiating password reset. Hackers use the predictability of username formats and procedures to access vehicle. For instance, BMW customer services recommended setting usernames as first dot last name, resulting in predictability and ease of access, as drivers often inadvertently shared this information on social media. This is a humbling reminder to us all to protect our personal login details by safeguarding the publicity of our information, and for companies to consider security when creating login pages as they are in as much danger to hacking as the users are.
Expanding beyond BMW, vulnerabilities were found in early hybrids like the Mitsubishi Outlander Hybrid, reflecting the industry's embrace of hybrid technology driven by a growing demand for environmentally friendly options.
Ken also investigated the Wi-Fi hotspot in a Mitsubishi vehicle, where he found a security issue with the unchangeable Wi-Fi key, making it vulnerable to hackers. By analysing network traffic, he realised that simple commands (such as ‘10’) could remotely control vehicle functions, such as turning on lights. Through reverse engineering the mobile app, he discovered a method to disable the theft alarm from a laptop, which you presents an alarming cyber security issue.
Exploring beyond vehicle theft, Ken and his team researched the misuse of additional aftermarket functionalities, particularly high-end smart and connected car alarms advertised as un-hackable. However, marketing such devices as resistant to hacking posed a challenge, igniting Ken’s curiosity. Investigating how these alarms interface with mobile apps, he uncovered vulnerabilities like Insecure Direct Object references, allowing hackers to compromise user accounts and gain access to the car alarm interfaces by triggering password resets then rerouting the reset emails to their own email address. This gave the hacker control with ease.
In a concerning turn, they found themselves not only inside the car but also able to code a key—a process as simple as connecting to Wi-Fi, cracking the key within minutes, and determining the correct commands. This provided the ability to disarm alarms and even track Outlanders across the country to their precise locations, presenting a serious security risk.
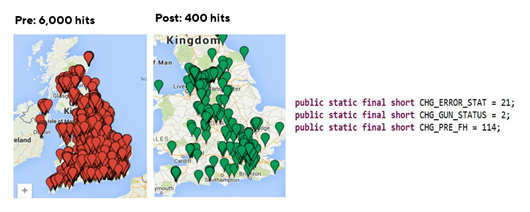
Hacking entry points and methods are increasing.
Below we have outlined some of the popular methods and entry points for exploitation of vehicles to engage in theft. These include:
- Connected Devices: Vulnerabilities have been found in various connected devices, such as EV home chargers, Smart TVs and even refrigerators. These devices provide potential entry points for hackers to access networks or control systems remotely. These can include Jamming, Bluetooth dongles, Smart speakers, mobile apps devices and so much more. Hackers are becoming more advanced in the techniques they utilise as protective security measures are introduced by motor supplier.
- Connected Vehicles: There are numerous vulnerabilities discovered in connected vehicles, including those related to mobile apps, Wi-Fi connections, telematics control units, and onboard diagnostic ports. These vulnerabilities allow hackers to gain control over vehicle functions, steal cars, or even compromise corporate networks through the vehicle's systems.
- Telematics Platforms: Thieves have begun exploiting vulnerabilities in telematics platforms, which connect vehicles to the internet and allow for remote monitoring and control. Hackers can potentially access sensitive information or take control of vehicles through these platforms.
- Charging Infrastructure: Security flaws in both home and commercial electric vehicle chargers, which could be exploited to disrupt charging operations or even cause power grid instability and even a nationwide blackout.
OEMs/Manufacturers
Original equipment manufacturers (OEMs) and vehicle manufacturers face real challenges to ensure the cybersecurity of connected vehicles. Despite advancements in security measures, the legacy issue is a significant hurdle. With vehicles having lifespans of a decade or more, it takes time for newer, more secure vehicles to replace older ones in the market. Additionally, the complexity of updating vehicles in the field poses a challenge. Ken’s observations emphasise the importance for OEMs and manufacturers to prioritise cybersecurity in both new vehicle designs and retrofitting older models with enhanced security features to mitigate the risks associated with legacy systems.
Additionally, Ken provided an example of how car theft, enabled through the manipulation of GPS trackers, disrupts shipping operations because of GPS jammers being used. This reveals the ripple effects that cybersecurity issues in vehicles can have on other industries and infrastructure. As autonomous vehicles become a more prominent part of the motor landscape, the potential for cybersecurity threats to impact their functionality and safety becomes increasingly critical. OEMs and manufacturers must address these vulnerabilities comprehensively to ensure the trust and safety of consumers in the evolving motor landscape.
Advanced methods – telematics, API, corporate domains
Ken demonstrated how exploiting weaknesses in the telematics control unit (TCU) via SIM card manipulation could breach corporate networks through a vehicle's systems. He also uncovered security flaws in both residential and commercial Electric Vehicle (EV) chargers, posing risks to the power grid and making charging infrastructure vulnerable to cyberattacks. Despite improvements in cybersecurity, older vehicles remain susceptible to direct Controller Area Network (CAN) attacks, leading to the adoption of safeguards like Radio-frequency identification (RFID) pouches to prevent key relay attacks. Ken also discussed unintended consequences, including GPS interference affecting shipping navigation and the danger of spoofing autonomous vehicle sensors. He highlighted the ongoing challenge of achieving fully autonomous driving due to persistent cybersecurity vulnerabilities in motor systems.
EV charging networks
There are obvious vulnerabilities in various aspects of technology, including EV charging networks. He demonstrated serious security flaws in both residential and commercial EV chargers, highlighting the potential for destabilising the power grid and facilitating cyberattacks. Through his investigations, he revealed the ability to remotely control and manipulate millions of chargers, posing risks to EV drivers and the broader energy infrastructure. These vulnerabilities underscore the urgent need for robust cybersecurity measures to safeguard EV charging networks against exploitation and ensure the reliability and security of electric vehicle charging infrastructure.
An underwriter’s view.
To add an underwriter’s view, Mark Suffield, Regional Trading Underwriter in our Prestige team emphasised a proactive approach to mitigating evolving risks in vehicle theft, particularly concerning electronic compromise. Recognising the shifting landscape where even high-value vehicles are increasingly targeted by technologically adept thieves, Mark stressed the importance of collaboration with experts like Ken to stay ahead of emerging vulnerabilities. The current focus is on endorsing aftermarket immobilisation devices like Thatcham Cat 2 immobilisers, complemented by Automatic Driver Recognition (ADR) trackers, to physically prevent theft rather than relying solely on post-theft recovery measures. While confident in the current strategy's effectiveness, Mark underscores the need for ongoing vigilance, risk selection, and adaptation to emerging threats, recognising the dynamic nature of the challenge.
In response to the escalating theft trends, our strategy involves a combination of proactive measures such as deploying aftermarket immobilisers and ADR trackers to physically prevent vehicle theft. While acknowledging the effectiveness of these measures, Mark emphasises the necessity of continuous monitoring, adaptation, and collaboration with industry experts to address emerging vulnerabilities effectively. The strategy reflects a commitment to protecting both customers and the insurance company's exposure by staying ahead of evolving theft methods and maintaining a proactive stance toward risk management in the face of rapidly changing technological landscapes.
We’re here to support your business needs with our product education webinars and marketing support hub. Stay connected today.
Have a question? Get in touch now.






